Author: Spike
Editor: Jerry Crypto
DID: Decentralized Identity❎
DID: Dissociative Identity Disorder✔️
When we Googled DID, the first explanation is Dissociative Identity Disorder (DID) which is a medical term rather than the crypto concept(Decentralized Identity) we knew already. Compared to DeFi, GameFi, NFT, and DAO, DID is a highly neglected area that has not received enough attention from investment institutions and technology developers.
In the context of the Decentralised Society (DeSoc) with a richer and more diverse ecosystem, so we believe that DID is a key component of building DeSoc, but also a crucial portal to Web 3. Previously, we had pinned our hopes on the NFT’s unique characteristics to complete the identification in Web 3. In reality, however, some NFT artists and creators are bothered by plagiarism and fraud. For example, Rarible auctioned off the unlicensed artwork of Derek Laufman, the designer of Marvel's Super Hero Adventures. By its nature, it is arguably not Web 3 at all.
Due to DID being the hub of all digital, it is imperative to create a shared, flexible and resilient identity layer. As DIDs are adopted by more users and Dapps, all digital processing permissions are to be in the hands, of the one who is not confined to a single application system, multiple accounts and password records. Only based on DID Web3 empowerment like DeFi, GameFi, NFT and DAO, as well as other promising scenarios, it will blossom into a more exciting narrative.
The full research report is divided into three chapters:
Chapters two: A History of DID Development
The
following concepts are essential for the narrative, and it doesn't matter if
you disagree with, as they do not affect our understanding at all. The focus of
this section is on "a look back at what constitutes our use of the
Internet" as a way of exploring the future development of DID.
1. Where it all began: the
first appearance of the Web
Web
1.0:
the World Wide Web and the browser. First of all, we have to acknowledge the
basic fact that it was the concept of Web 2.0 that gave the World Wide Web its
"honorary" name.
It
was only after the network technology came out of the military laboratories and
research institutes that we had the so-called Internet, and at this time, the
entrance was the browser and the World Wide Web, which basically constituted
the whole concept of the web, and while it was things like RSS and BBS that
were the main scenarios behind the use of data. The IDs at this time were
mainly email addresses, personal domain names and forum IDs, with very clear
components.
2. The historical origins
of Internet privacy: the growth of personal data
Web
2.0 and UGC, Blogs, iPhone, 5G, XR
From
Blogs to Tik Tok, the right to personal expression went through a continuous
phase of decentralisation, from the beginning of the elite to a universal
media, from middle age to adolescence, the Internet became an a priori presence
in the Z-era, an unquestionable status, an airy and ubiquitous infrastructure
like water, electricity and coal.
As
we all know, the 2016 US election saw the outbreak of the sale of personal data
by Facebook, which was used by Cambridge Analytica to some extent to control
the US election. This is possible on the basis of two assumptions: firstly,
that people leave a large digital trail of their privacy on the internet; and
secondly, that people concentrate on leaving their personal data on certain
applications, such as Facebook and Twitter.
What
needs to be made clear is that the concept of personal data emerged first,
followed by the debate about privacy. The gradual migration of IDs to social
tools at this time does not mean the demise of the mailbox, but rather a change
in people's habits of use and, more appropriately, the emergence of Facebook as
an optional login tool in addition to the mailbox, provided that people use
Facebook by default for everyone.
But
the downside of this situation is becoming increasingly apparent today, our
data is held within apps like Google, Facebook etc. It may seem like we are
talking about our privacy, but in fact we are talking about our relationship
with these companies.
3. DID under Web 3: a
portal
Web
3.0 is a crossroads of concepts, which from the time the concept was introduced
in 2004, through the transformation of the traditional Internet and the gradual
establishment of a link to the blockchain. This connection was not made in one
step, at least through the (public chain) Bitcoin, Ethereum and EOS era, in an
attempt to replace the WWW with a public chain. This has effectively failed so
far, and the parallel chains of the Polkadot era that followed were an
admission that it was not feasible to have one chain for all.
When
we talk about blockchains, the various eras point to different things, from the
original Bitcoin to the later DeFi and NFT to today's Web 3.0, which does not
mean that the latter replaces the former, but more of a gradual overlapping
development between them.
Just
as we ordinary people now do not have to understand the TCP/IP protocol, the
principles of compilation, or the principles of computer composition in order
to use a device to access the Internet, we do not know in the incubation phase
of building Web 3.0 technologies what will be the final constituent elements
and what will eventually be discarded as floating dust. But humanity will
eventually progress and grow towards the digital age in the use of Web 3.0, and
then we will now be convinced of the importance of DIDs. There will always be a
portal, and it won't be a portal.
In
Satoshi Nakamoto's vision, it would be better for people to use one address per
transaction, which would provide maximum privacy. But the truth is that no one
does this every day except hackers and people who forget their Mnemonic Phrases.
We are used to using a single address for a long time rather than a single
address every time; more importantly, the blockchain has evolved beyond Satoshi
Nakamoto's "blockchain".
But
in interactability and decentralisation, there must be a finite number. This is
similar to social tools, where a true infrastructure creates strong user
stickiness, especially in the decentralised world.
Web
3.0 will embrace much of the plays, absorbing concepts such as blockchain,
DeFi, NFT and together forming the next generation of the internet, meanwhile
DIDs will become the most direct port for interaction. It is necessary, then,
to list the paths by which DIDs are likely to become:
(1)L1: Identifiers and
Standards
Standards,
Identifiers and Namespaces work together to build the public trust layer,
ensuring standardisation, portability and interoperability.
This
section also defines how DIDs are registered and used to manage them, providing
developers and users with rules and environmental standards for accessing the
web identity system.
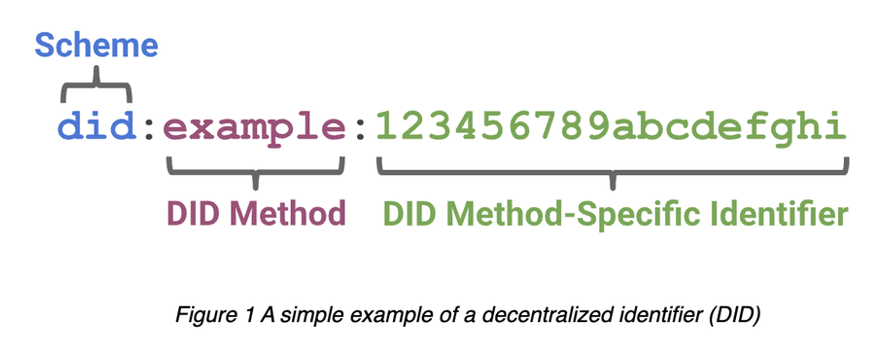
Source: the W3C
The
most typical here is the DID standard drafted by the W3C, dating back as far as
2019, where the draft document states that "each DID document may
represent cryptographic material, an authentication method, or a service
endpoint. These documents provide a set of systems that enable the DID
controller to demonstrate control over the DID. And, the service endpoint
enables trusted interaction with the DID."
Overall,
this was a milestone in the history of DID in that we acknowledged for the
first time that DID was feasible and attempted to outline its general direction
and framework, but in terms of subsequent developments, none of the existing
projects have adopted this standard, so we will not go into the details of it.
(2) L2: Infrastructure
Having
recognised the importance of DIDs, we have begun to explore how they should be
designed, but one thing is certain: they will become an infrastructure, closer
to the underlying concept of an API or SDK.
This
is because a DID as infrastructure and proxy framework would allow
bi-directional or even multilateral interaction between applications, even
between DIDs and DIDs, and interconnecting data and information at a protocol
level, as well as allowing applications to interact directly with a registry of
verifiable data.
The
DID in this concept should at least include communication, storage and key
management, and if it goes further, it can be "de-passworded" while
retaining login and authentication functions.
Here
is a look at what such an infrastructure might look like in the context of the
traditional Internet.
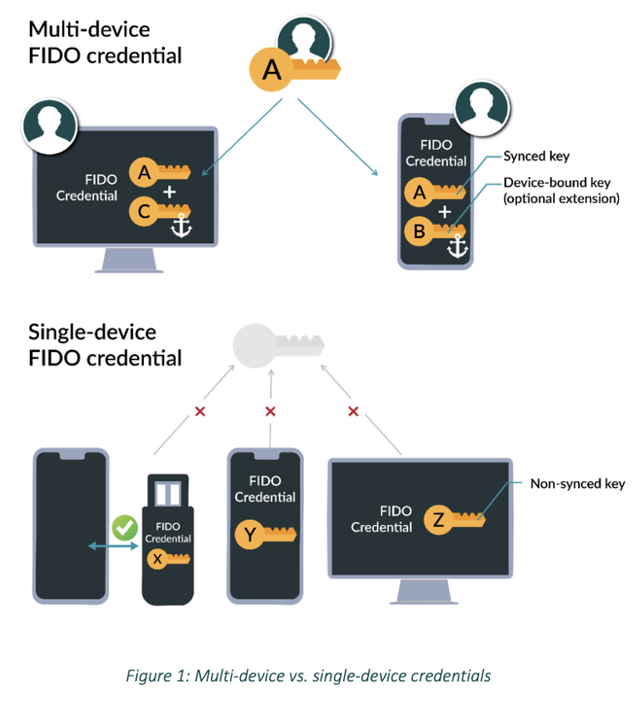
Source:FIDO
For example, FIDO, a concept that
Apple also officially started supporting at WWDC 2022, we briefly describe the
steps for its use:
(1) Using your phone as a roaming
authenticator
(2) Sharing Multi-device FIDO
credential
In theory, FIDO can also be cut
into the future of Web 3.0 networks. This crypto technology with
once-authenticated, password-abandoning, multi-device use is ideally suited for
the network infrastructure in the future.
(3) L3: Credentials
FIDO
is ultimately a product of Web 2.0 and is not necessarily fully adapted to the
needs of Web 3.0. We need to manage and update identity credentials, and they
need to be interchangeable. This layer aims to address how the DID determines
the "proof of control" and "proof of authentication", and
how to securely pass data between identity owners.
In
fact, there are already attempts at this concept, such as DAS (Decentralized
Account Systems), a decentralized account system that does not rely on a
specific public chain and supports multi-public chain and multi-protocol
interactions.
The
idea behind DAS is to swap individual addresses to a system of unique accounts
ending in .bit, which are themselves decentralised and can be used
directly as account addresses to receive payments, login and of course as
access portals to Dapp. This is essentially a secondary innovation based on the
DID concept, which is a more underlying protocol than applications such as
wallets.
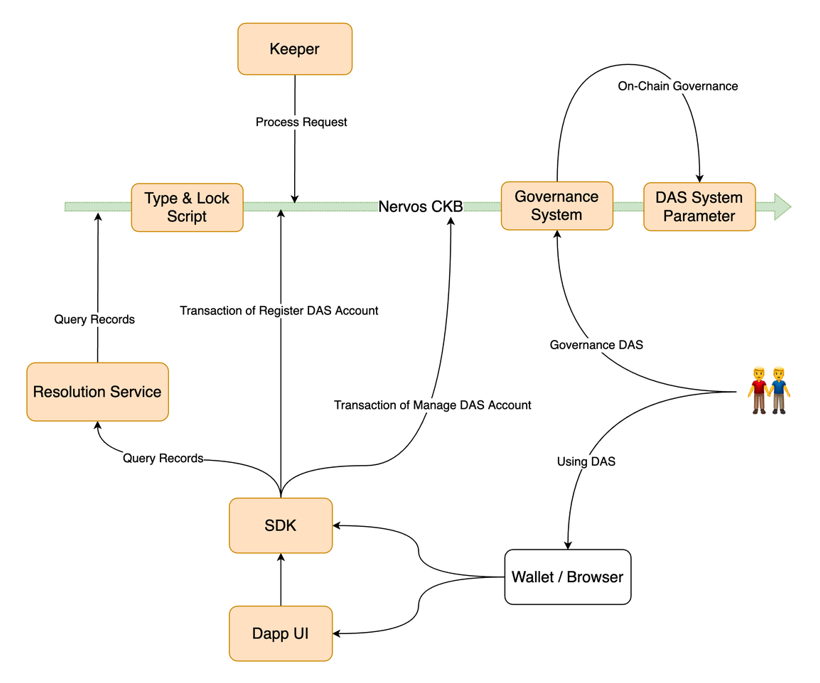
Source: DAS
But
this begs the question, is this a DID or not, or what is the difference between
DID and wallet? You know, wallets are hard to remember, but Dapp login and
interaction within the wallet is very smooth. So this could be used as an idea
for reference, but it's hardly mainstream.
(4) L4: Wallet and Dapp
This
layer is the most familiar. In addition to the MetaMask mentioned above, there
are projects such as Goldfinch (Loans without collateral) that use proprietary
and unique entity checks, but this will only use them when the DID technology
is mature. In other words, it is the idea of waiting until the DID system is
mature enough and the number of users is large enough for it to work. In
contrast, other applications are already using existing DID technology, such as
TrueFi (powered by the first ever on-chain credit scores ), Gitcoin
(blockchain-based incentivization layer for open source software) and Ethsign
(decentralised electronic protocols).
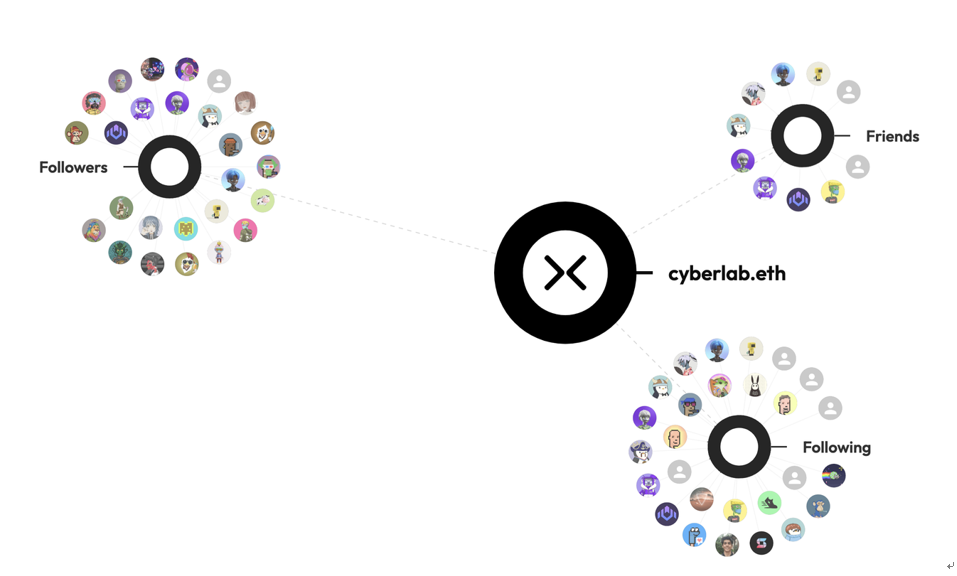
Source: CyberConnect
A
more viable idea is CyberConnect, which is similar to the WalletConnect
development idea for wallets. "What if I can't beat MetaMask, but there
are other wallets at the same time?" Simple, bring them together at the
protocol level so that Dapp developers only need to set aside development time
for MetaMask and WalletConnect.
CyberConnect
is exactly the same idea, "I don't really know what kind of social
products people will be using and what they will be doing on the web in the
future Web 3.0, but in short, they need a protocol like this."
This
would turn into a DID + aggregator, forming a social graph of information for a
certain address, which all comes from on-chain data ending up as a more
front-loaded aggregator while avoiding competition with specific Dapps. For
example, we can use the address to retrieve information about a certain person
and at the same time view ourselves.
Is
that all there is to it?
Of
course not, as we gradually dive deeper and drop into the design logic of
specific products, we also need a more macro view of the future of DIDs.
(5) LX: DID for DeSoc
This
is something that goes beyond a single layer and has an impact on applications
on multiple layers, which may be a direction to look forward to in the future.
The current reference is the European General Data Protection Regulation(GDPR)
which has an impact on all areas of the ecosystem.
In the Web 3.0 space, it is more intuitive that this could be "soul binding", of which DIDs would be a direct example. ThePrimedia will cover this in the next article, so stay tuned for "Chapter 3: Another attempt to find yourself".